Snotra Lambda
Continuous AWS Testing with Snotra, Lambda, Cloud Watch EventBridge and S3.
I have recently pushed a change to Snotra, my AWS auditing tool, which enables it be deployed as an AWS Lamda function.
This post will explain how to deploy Snotra as a Lamba Function, schedule regular scans via a Cloud Watch Events and save the results to S3.
Create and Test Lambda Function
Create a Python lambda function
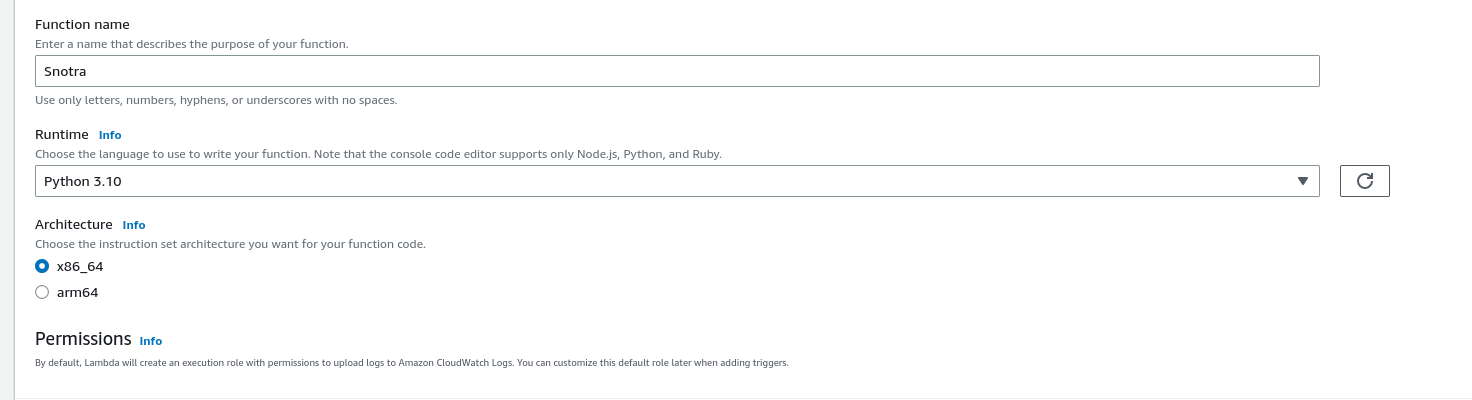
Download Snotra Zip file from source on GitHub
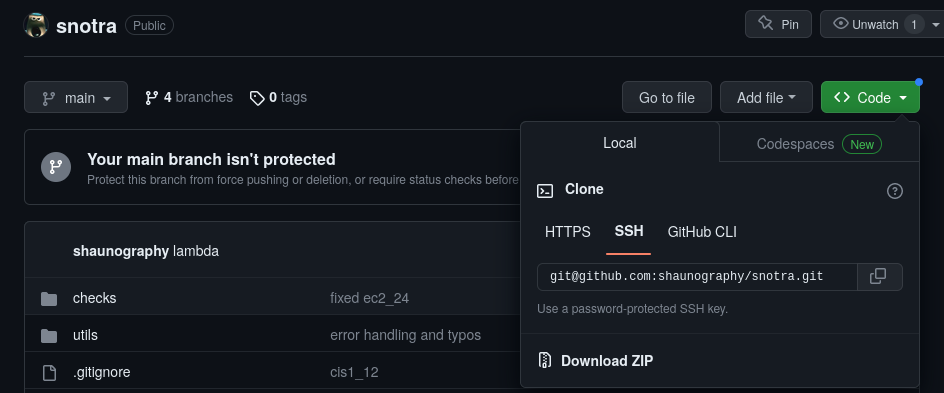
Upload source zip file to Lambda
Once it has uploaded the file structure will look like this
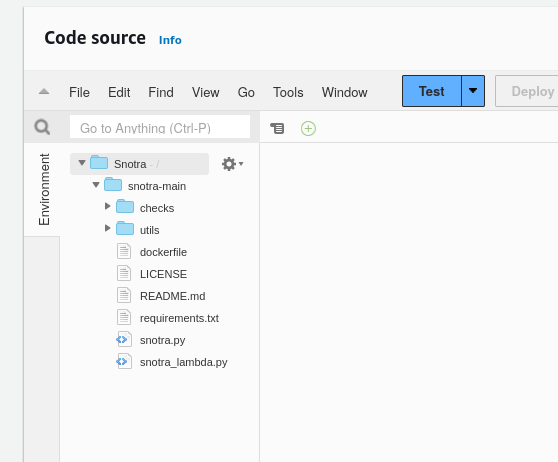
We need to move Snotra to the Snotra root directory, your file structure should then look like this
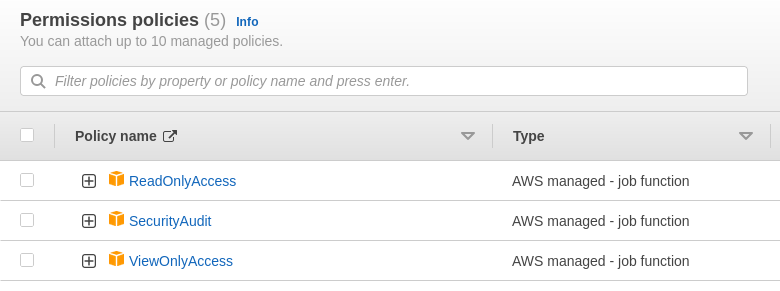
If you want Snotra to scan the local AWS account you will need to give the Lambda role the required permissions. Find the role assocaited with your new Lambda function in IAM and assign the following AWS managed policies:
- ReadOnlyAccess
- SecurityAudit
- ViewOnlyAccess
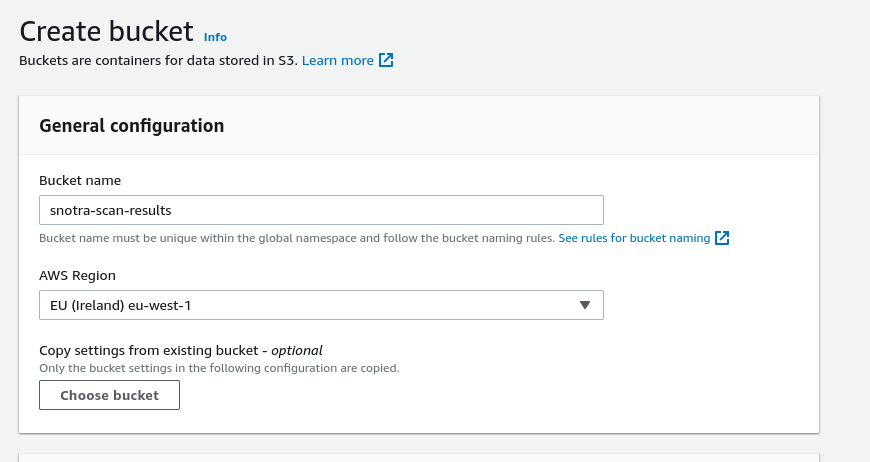
Create an S3 bucket to hold the results and update line 112 in the lambda function with the bucket name.
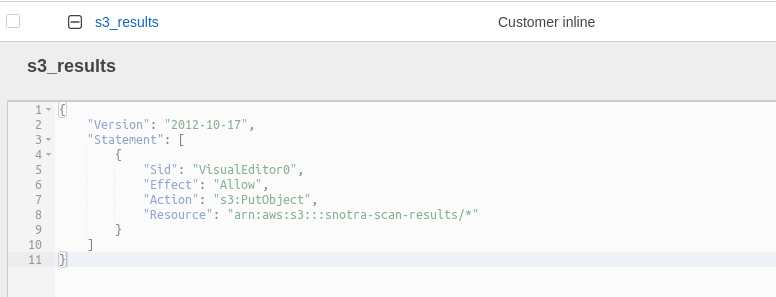
Give the Lambda role the required permissions in order to put files into the bucket.
Create an inline policy with the following JSON definition, updating the bucket name as required for your environment:
{ "Version": "2012-10-17", "Statement": [ { "Sid": "VisualEditor0", "Effect": "Allow", "Action": "s3:PutObject", "Resource": "arn:aws:s3:::snotra-results/*" } ] }
Configure the handler in the Lambda's runtime settings
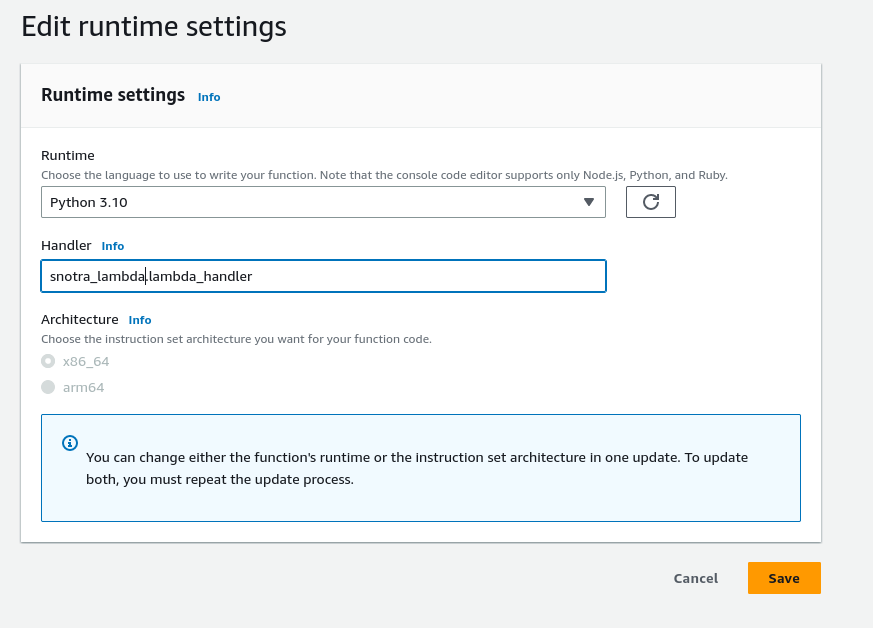
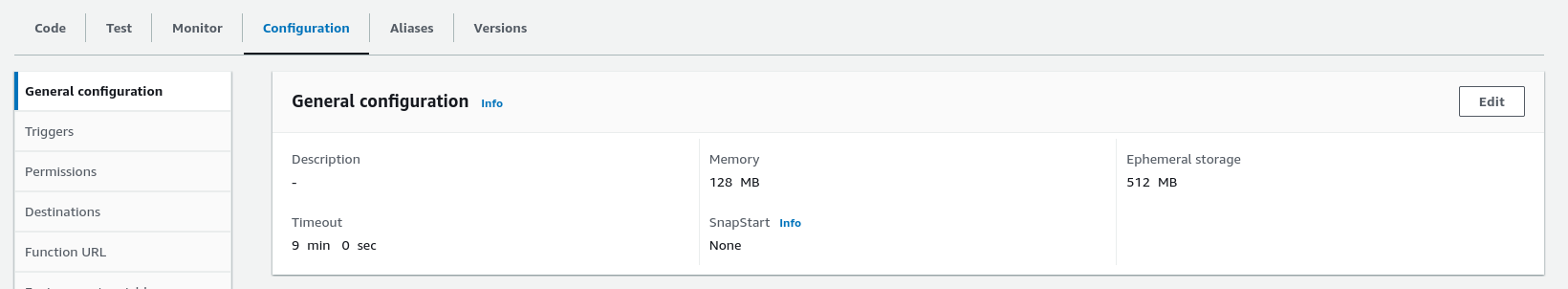
Under configuration > General configuration configure a suitable timeout, I use 9 minutes
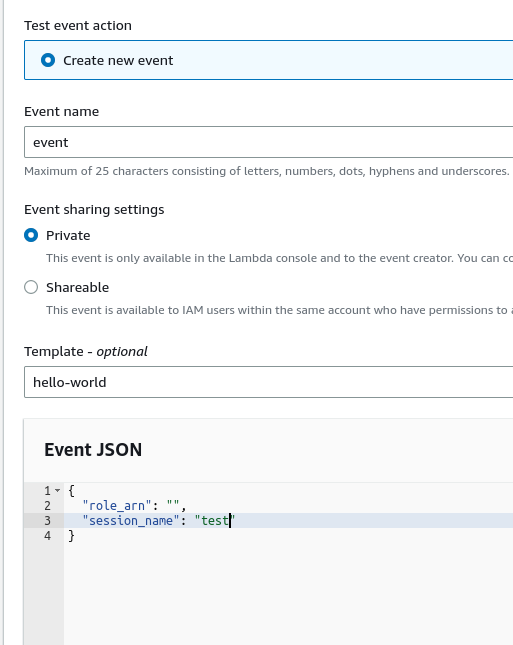
now we are ready to test the Lambda by creating a test event, use the following JSON to scan the local AWS account.
{ "role_arn": "", "session_name": "test" }
Create event
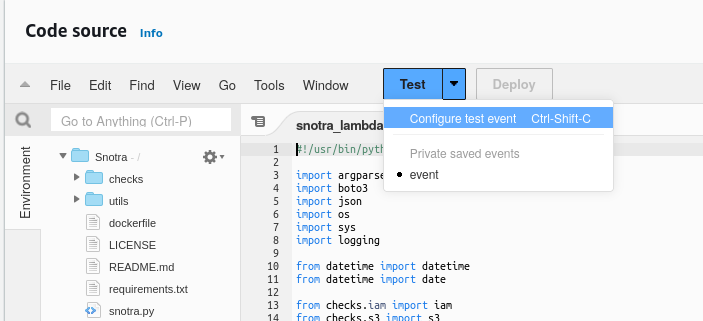
Execute test
If all goes well then the output should looks something like this
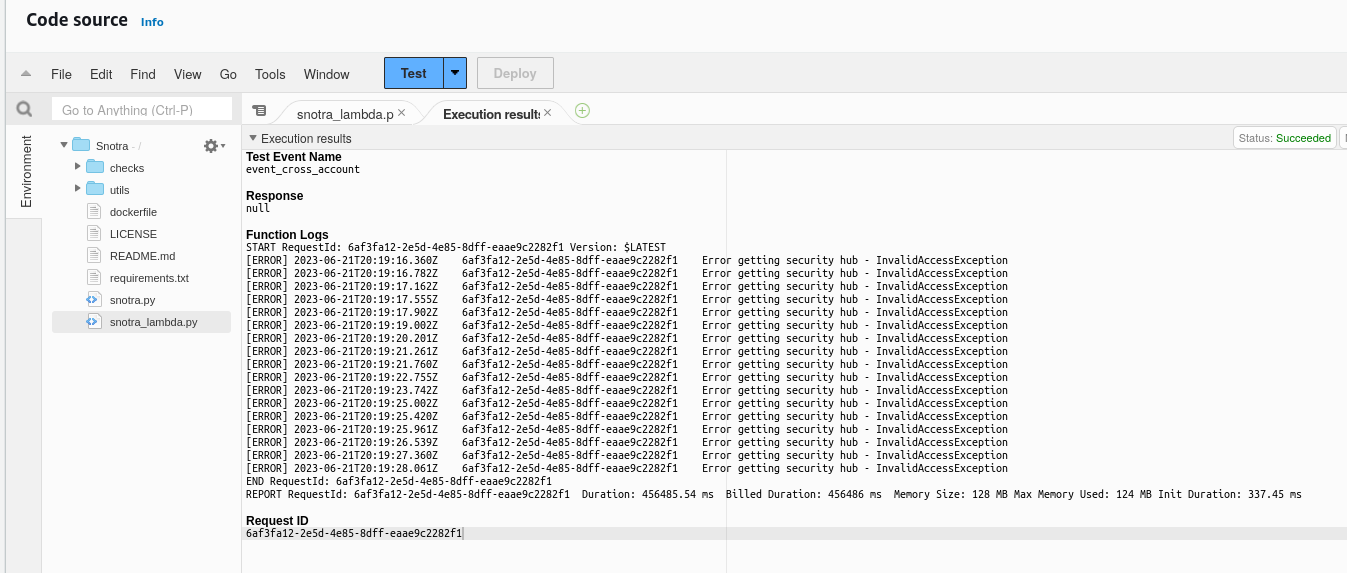
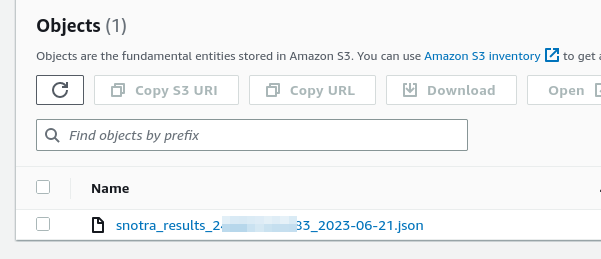
And the results should end up in S3
Cross Account Scanning
To scan other AWS accounts you need a cross account role in the target account and allow the lambda to assume it
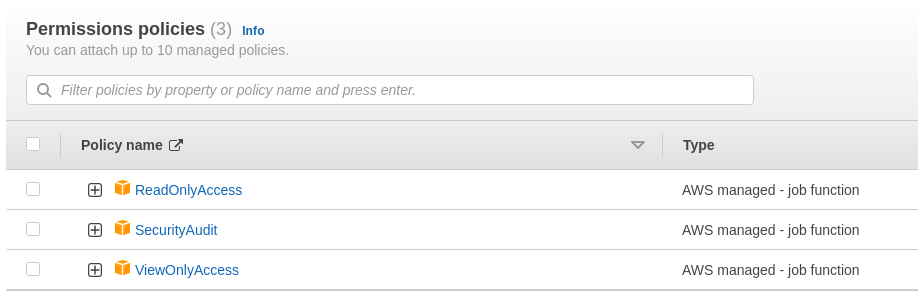
Create a role in the target account with the following AWS managed policies:
- ReadOnlyAccess
- SecurityAudit
- ViewOnlyAccess
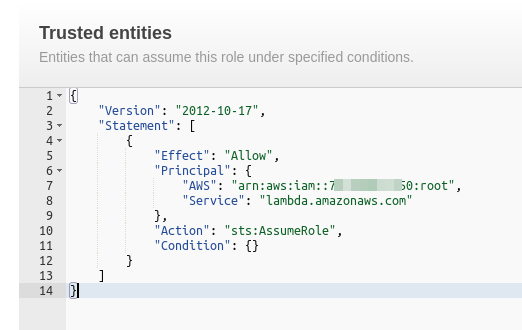
Use the following JSON to Configure the cross account trust policy updating your account ID
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Principal": { "AWS": "arn:aws:iam::000000000000:root", "Service": "lambda.amazonaws.com" }, "Action": "sts:AssumeRole", "Condition": {} } ] }
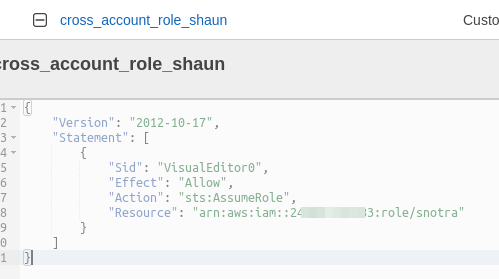
Add an inline IAM policy to the Lambda functions role with the following JSON definition, giving it permissions to assume the role in the target account
{ "Version": "2012-10-17", "Statement": [ { "Sid": "VisualEditor0", "Effect": "Allow", "Action": "sts:AssumeRole", "Resource": "arn:aws:iam::000000000000:role/snotra" } ] }
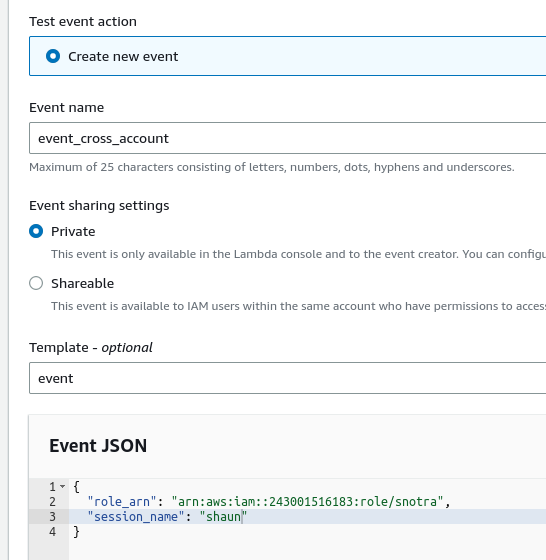
Create new test event for cross account scan
Kick off a test, if all goes well the output should look something like this

And the results should end up in S3

CloudWatch event
Now we are going to configure a Cloud Watch event to trigger the Lamba on a schedule
Go to CloudWatch EventBridge > Rules > Create Rule
Give the rule a relevant name and description and select the schedule rule type
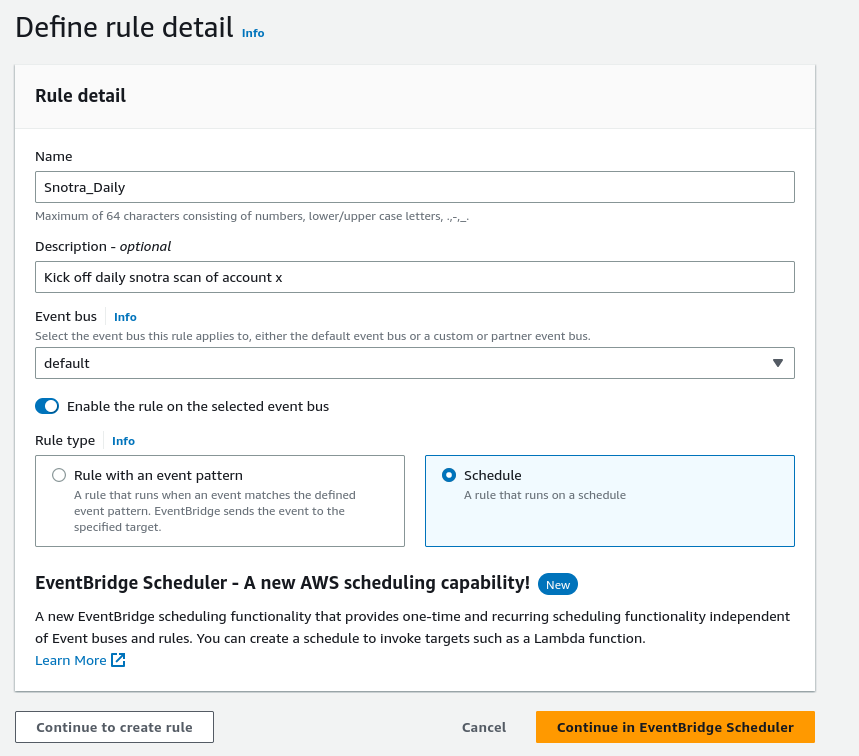
Configure your event schedule as required

Select AWS Lambda Invoke as the target
Select your Snotra Lambda function and use the following JSON payload as we did before for the test events
{ "role_arn": "arn:aws:iam::000000000000:role/snotra", "session_name": "shaun" }

Click through the rest of the options and create the schedule
Everything is now configured, your schedule will trigger the lambda function, a scan will be run and the JSON results will be accumulated in the S3 bucket for ingestion and use with other tools and workflows.

About the author
Shaun is a Penetration Tester and Bitcoiner based in state controlled Britain, with over a decade in the Security Industry, specialising in Cloud and Infrastructure Security and regularly completing assessments for all manner of companies from global corporations to small charities and non profits.